Imagine a digital world where different financial systems operate in complete isolation. Each system has its own unique currency and rules. Assets from one system are technically locked away and cannot be used in another. This was the reality for early distributed networks.
Specialized infrastructure emerged to solve this problem. These solutions create vital connections between separate ecosystems. They allow value and information to flow freely where it couldn’t before. This breaks down the walls that once divided the digital landscape.
The demand for this connectivity is massive. As of 2025, over $55 billion in value is locked in these protocols. This shows a strong market need for a truly interconnected online world. These connections are essential for the next generation of the internet.
Key Takeaways
- Different distributed networks originally operated as isolated systems with non-transferable assets.
- Specialized protocols were developed to enable communication and transfer between these separate networks.
- This technology facilitates not just asset movement but also data exchange across different systems.
- The digital ecosystem is now multi-network, with hundreds of distinct platforms and scaling solutions.
- Significant financial value, exceeding $55 billion, is currently secured within these connecting protocols.
- This infrastructure is critical for user freedom, preventing lock-in to any single digital ecosystem.
Understanding Blockchain Bridging: The Basics
To move value between sovereign digital nations, a new kind of infrastructure was required. These platforms solve the problem of network isolation. They create pathways for assets and data to flow freely.
What Are Blockchain Bridges?
Think of these protocols as dedicated messengers. They are specialized applications designed to facilitate the transfer of assets from one ecosystem to another. This process unlocks liquidity that was previously stuck.
These solutions can operate under different models. Some are decentralized, while others are centralized or use a hybrid approach. Each model carries its own set of trust assumptions for users.
Key Concepts and Terminology
Understanding a few terms is essential. The source chain is where an asset originates. The destination chain is where the asset is sent.
The primary goal is to achieve cross-chain liquidity. This allows tokens to be useful across multiple environments. It significantly increases their utility and potential.
This technology handles more than simple currency moves. It also enables the transfer of NFTs and smart contract commands. This creates a truly interconnected online experience.
cross chain blockchain bridges how they work
The technical foundation for moving digital assets across separate ecosystems relies on a carefully orchestrated sequence of events. This process enables value to flow where it was previously inaccessible.
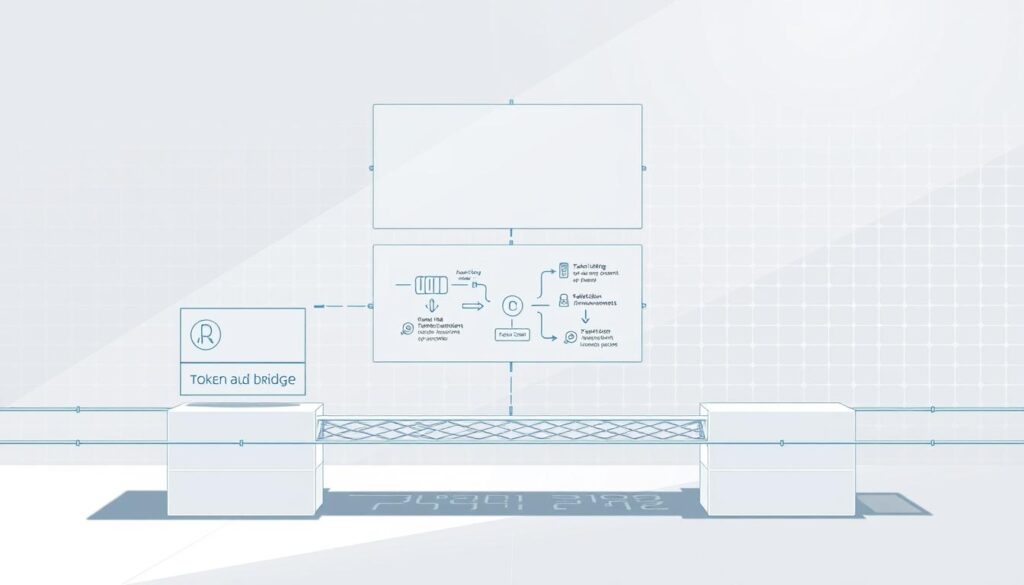
Overview of the Bridging Process
The most common method follows a lock-and-mint approach. Users initiate the process by depositing their assets into a specialized contract on the originating network.
A validator group or custodian then secures these assets in a digital vault. Simultaneously, equivalent wrapped tokens are created on the target network.
This creates a representation of the original asset that maintains value parity. The entire operation is automated through smart contracts that handle locking, minting, and eventual redemption.
Interoperability in Distributed Networks
True interoperability requires coordination mechanisms that can verify state across independent systems. These protocols must ensure accurate synchronization between the source chain and destination chain.
The wrapped tokens method demonstrates how value can be preserved during transfers. This approach allows assets to gain utility across multiple environments without actual physical movement.
Different blockchain networks maintain their sovereignty while gaining connectivity. This technical framework supports the growing ecosystem of decentralized applications.
Mechanisms Behind Asset Transfers
The underlying mechanics that power asset movement rely on either synthetic token creation or pooled reserves. These approaches enable seamless value movement between independent networks.
Wrapped Asset Method Explained
This approach uses a smart contract to lock original tokens on the source network. The locked assets are removed from circulation temporarily.
Equivalent wrapped tokens are then created on the destination network. These synthetic representations maintain value parity with the original assets.
When returning assets, the wrapped tokens are destroyed. This burning process triggers the release of the original assets from the smart contract.
Utilizing Liquidity Pools
Some protocols like Synapse maintain reserves of assets on multiple networks. These pools function like digital banks holding native tokens.
Users receive actual native assets rather than wrapped versions. The system draws from pre-funded reserves on both networks.
Protocols incentivize liquidity providers through staking rewards. Users lock their assets into pools and earn periodic returns.
Three primary technical models exist: lock-and-mint creates wrapped representations, burn-and-mint recreates native tokens, and lock-and-unlock uses pooled reserves. Each method balances capital requirements with user experience.
Types of Crypto Bridges and Their Security Models
The security and control models of interoperability protocols define their fundamental trust assumptions. These models determine who controls assets during a transfer.
Understanding this distinction is crucial for assessing risk and aligning with personal preferences for convenience versus maximum self-custody.

Trusted Bridges vs. Trustless Bridges
Trusted bridges are operated by a central entity or federation. Users surrender control of their assets to this authority during the process.
This model prioritizes speed and lower transaction fees. The Binance Bridge is a well-known example that leverages exchange infrastructure.
However, this convenience comes with a trade-off. Users must trust the entity’s integrity and operational security completely.
In contrast, trustless bridges eliminate the central intermediary. They rely on algorithms and smart contracts to facilitate transfers.
This approach gives users full control over their funds, embodying the core principle of decentralization. The underlying code and cryptography provide the security.
Moving toward greater trust-minimization, however, often increases complexity and cost. It can also limit the flexibility of the protocol.
Choosing between these models depends on what a user values most: the efficiency of a trusted system or the self-sovereignty of a trustless one. For a deeper dive into the different types of blockchain bridges, including hybrid models, further exploration is valuable.
Blockchain Bridging Use Cases in Web3
Beyond the technical mechanics, these connection protocols deliver tangible benefits that power the modern decentralized ecosystem. Their practical applications extend across various scenarios that enhance user experience and functionality.
The $55 billion in locked value demonstrates the substantial utility these technologies provide. They serve both individual users and enterprise-level operations with equal effectiveness.
Transferring Assets Across Blockchain Networks
The primary function enables users to move digital holdings between separate environments. This allows someone to utilize Ethereum-based assets on Solana without selling and repurchasing.
This process maintains asset value while expanding utility across multiple platforms. Users gain access to opportunities that were previously inaccessible.
Enabling Access to Diverse dApps
Each digital environment hosts unique applications with specialized features. Connection protocols let users explore these diverse offerings without liquidating their original holdings.
This expands the available toolkit for decentralized finance and other applications. Users can participate in ecosystems that best suit their specific needs.
| Use Case | Primary Benefit | Example Scenario |
|---|---|---|
| Asset Movement | Access to different opportunities | Using Ethereum holdings on Solana dApps |
| Liquidity Routing | Better price discovery | Large trades with reduced slippage |
| Yield Optimization | Asset productivity | Moving to chains with higher returns |
| Enterprise Payments | Multi-chain settlement | Companies paying merchants on preferred networks |
These protocols typically offer lower fees compared to traditional exchange methods. Enterprise applications include stablecoin payments across different settlement preferences.
Risks and Security Challenges in Blockchain Bridges
The very features that make interoperability solutions valuable also create attractive targets for malicious actors seeking to exploit vulnerabilities. These connection points handle enormous amounts of value, making them high-priority targets for sophisticated attacks.

Centralized Theft and Smart Contract Vulnerabilities
Trusted models carry inherent risks where controlling entities could theoretically access user funds. While legitimate projects maintain integrity, the possibility exists.
Even trustless systems face code-level threats. A single bug in smart contracts can lead to catastrophic losses, as demonstrated by major exploits.
Cybersecurity and Phishing Threats
Scammers create fake websites that mimic legitimate platforms to steal crypto during deposit. Users must verify URLs carefully to avoid these sophisticated schemes.
Phishing attacks remain prevalent in the decentralized space. Always use bookmarked official links rather than search results.
Research shows over $2.8 billion has been stolen from these protocols. Major incidents include Ronin ($522M) and Wormhole ($320M) exploits.
Comparing Cross-Chain Bridges and Centralized Exchanges
When moving digital assets between different networks, users face a critical choice between two primary methods. While both achieve similar outcomes, their approaches and implications differ significantly.
Centralized platforms like Binance and Coinbase offer cross-chain functionality through asset conversion. Users sell holdings on one network and purchase equivalent assets on another. This multi-step process involves deposit, trade, and withdrawal phases.
Cost Efficiency and Transaction Speed
Bridges typically offer superior cost efficiency. A single transaction handles the entire transfer process. This avoids the cumulative fees of exchange trading, withdrawal, and network gas costs.
Speed represents another significant advantage. These protocols complete transfers in minutes rather than hours. Exchange processes require waiting for confirmations and manual trade execution.
Airdrop eligibility provides additional value. Many projects reward decentralized on-chain interactions. Centralized platform transactions don’t qualify for these ecosystem rewards.
Decentralization appeals to users preferring self-custody. Bridges maintain private key control throughout transfers. Exchanges require temporary asset custody during the conversion process.
However, exchanges remain preferable for specific scenarios. Converting between different assets rather than bridging identical tokens benefits from exchange liquidity. Regulatory compliance may also favor licensed platforms.
Innovative Developments in Cross-Chain Interoperability
Next-generation connectivity protocols are reshaping how digital ecosystems communicate and transfer value. These advanced solutions address the growing need for secure messaging between distributed systems.
The Emergence of Chainlink CCIP
Chainlink’s Cross-Chain Interoperability Protocol represents a significant leap forward. This open-source standard establishes universal connections between hundreds of networks through a single interface.
The system enables arbitrary messaging beyond simple asset transfers. Developers can send any data type between different environments, not just cryptocurrency holdings.
Programmable token bridges combine asset movement with smart contract execution. This allows automatic actions on destination networks involving transferred tokens.
Enhanced security features include a dedicated Risk Management Network. This independent system monitors for suspicious activity and can halt potentially malicious transactions.
The protocol leverages Chainlink’s proven oracle infrastructure, securing $59 billion in on-chain value. Off-Chain Reporting (OCR 2.0) enables efficient, decentralized validation of cross-chain operations.
Real-world implementations demonstrate practical utility. PayPal uses this technology for PYUSD stablecoin payments across multiple networks to accommodate merchant preferences.
| Feature | Traditional Bridges | Programmable Bridges |
|---|---|---|
| Data Transfer | Limited to assets | Arbitrary messaging |
| Automation | Manual processes | Smart contract triggers |
| Security Model | Basic validation | Risk Management Network |
| Developer Flexibility | Restricted functionality | Custom programmable actions |
These innovations represent the evolution toward more secure, flexible interoperability solutions. They will power the next generation of Web3 applications with enhanced capabilities.
Future Trends for Blockchain Bridges in Web3
Tomorrow’s digital infrastructure will prioritize user experience over technical complexity. The evolution of interoperability solutions is accelerating toward seamless multi-network interactions.
Current systems handle over $55 billion in locked value. This massive adoption drives innovation toward more intuitive interfaces.
Evolving Protocols and Security Enhancements
The trend toward chain abstraction creates experiences where users interact without knowing which network runs in the background. People sign one transaction while sophisticated backend systems handle multi-chain settlement automatically.
General message passing protocols enable more than simple asset movement. They allow arbitrary data communication between smart contracts on different chains.
Security improvements include decentralized validator networks and formal verification of bridge code. These enhancements address the vulnerabilities that have caused significant losses in the past.
Specialized solutions are emerging for specific use cases. NFT-focused bridges and enterprise-grade options with compliance features represent this specialization trend.
Builders who master this infrastructure today will lead tomorrow’s chain-abstracted world. The future points toward invisible, instantaneous connectivity across the entire digital ecosystem.
Conclusion
What began as experimental technology has matured into essential infrastructure for the entire digital asset space. These bridges now serve as critical touchpoints for moving value between separate networks.
A significant portion of DeFi trading volume flows through these protocols. This demonstrates their central role in modern cryptocurrency markets.
Security remains paramount for developers. Comprehensive smart contract audits and dApp security assessments protect user funds across different systems.
Understanding cross-chain compatibility is essential for anyone engaged with Web3. These connections enable the multi-chain future of distributed technology.
FAQ
What is a cross-chain bridge?
A cross-chain bridge is a protocol that connects two separate blockchain networks, allowing for the transfer of tokens and data between them. It enables different distributed ledgers to communicate, fostering a more interconnected ecosystem.
How does a blockchain bridge transfer assets?
Most bridges use a method involving wrapped assets. When you send a token, it is typically locked in a smart contract on the source network. An equivalent, or “wrapped,” version of that token is then minted on the destination chain for you to use.
What is the difference between trusted and trustless bridges?
Trusted bridges rely on a central entity or federation to operate, requiring users to trust that group with their funds. Trustless bridges use smart contracts and cryptographic proofs, allowing the system to operate in a decentralized manner without a central authority.
Are cross-chain bridges secure?
While innovative, these protocols face security challenges. Risks include smart contract bugs, which hackers can exploit, and phishing attacks targeting users. The security level depends heavily on the specific bridge’s design and the robustness of its code.
Why would I use a bridge instead of a centralized exchange?
Bridges often provide greater cost efficiency and faster transaction speeds for moving assets directly between networks. They allow you to remain in the decentralized finance (DeFi) space without converting to fiat currency, maintaining control of your private keys.
What role do liquidity pools play in bridging?
Liquidity pools are essential for many bridge models. They provide the immediate tokens needed on the destination chain, facilitating quick transfers. Users essentially swap their locked tokens for assets from this pool on the new network.
What is Chainlink CCIP?
Chainlink’s Cross-Chain Interoperability Protocol (CCIP) is a developing standard aimed at creating a secure and universal framework for messaging and token transfers across multiple chains, potentially reducing fragmentation in the ecosystem.

No comments yet