Stablecoins anchor value in volatile markets by tying tokens to a reference, often the US dollar. Over 27.5 million active users now rely on these assets as transaction volumes rise about 50% year over year. This guide shows why an intelligence layer matters for trust and peg maintenance.
AI-powered systems merge on-chain contracts with off-chain analytics to improve stability and restore price quickly after shocks. Rigid rule sets failed in past stress events; adaptive models use forecasting, sentiment signals, and filtered oracles to reduce failure modes.
Readers in the United States will find practical steps for on-chain design, data pipelines, oracle choices, and governance. Expect a hands-on playbook that balances engineering, risk controls, and measurable outcomes aimed at deeper liquidity and verifiable value preservation.
For an applied development roadmap, see this AI-powered stablecoin development reference.
Key Takeaways
- Stablecoins need intelligent controls to keep price and trust as users and volume grow.
- AI + smart contracts move systems from reactive rules to proactive stability tools.
- Focus areas: on-chain contracts, off-chain models, oracle design, and governance mechanics.
- Core goals: tighter peg control, faster recovery, deeper liquidity, and transparent value checks.
- This guide targets U.S. builders seeking secure, compliant, and scalable designs.
What You’ll Learn and Why It Matters Today
Here we define the core outcomes you should expect when evaluating AI-backed peg defense and liquidity tools.
Goal: gain a working model to apply adaptive controls that reduce de-pegging and measure results under live market stress.
AI-powered stablecoins use continuous monitoring of on-chain activity, market feeds, and external signals like macro news and social sentiment. These inputs enable real-time adjustments to defend a peg, manage liquidity, and support yield operations that preserve value.
User intent: understand, evaluate, and implement adaptive stability
This guide helps founders, engineers, and product leaders weigh trade-offs between hybrid collateral, rule-based designs, and AI-enhanced controls. It clarifies implementation steps: data ingestion, model selection, simulation, on-chain integration, and incident response.
Where this fits in the 2025 DeFi ecosystem
AI-stabilized assets slot into bridges, AMMs, money markets, payment rails, and cross-chain settlement layers. Better price stability cuts downstream risk for lending, LP strategies, and payments during high volatility.
| Benefit | What it protects | Key metric |
|---|---|---|
| Faster recovery | Peg deviations | Peg deviation < 1% |
| Lower intervention | Operational risk | Mean time to response (minutes) |
| Improved liquidity | Market depth | Depth at best bid/ask |
| Regulatory readiness | Auditable decisions | Logged model actions |
Foundations: From Stablecoins to Algorithmic and AI-Powered Models
Foundations matter: different designs use distinct assets and rules to protect a peg under stress. Choosing whether a token is fully backed, purely algorithmic, or hybrid shapes how it is designed to maintain value.
Collateralized, algorithmic, and hybrid approaches at a glance
Fully collateralized systems hold fiat, crypto, or commodities as backing. Examples include USDC and USDT for fiat-backed, DAI for crypto-backed, and commodity-backed variants. Over-collateralization helps absorb volatility when backing assets fall.
Pure algorithmic stablecoins adjust supply and incentives to defend the peg. These models can be capital efficient but rely heavily on market confidence; failures like Terra/UST exposed supply spirals and rapid de-pegs.
Hybrid models combine reserves with rules-based adjustments. FRAX is a common example: a buffer of collateral plus automatic mechanisms reduces tail risk while keeping efficiency.
Why rigid rules failed and how adaptive systems help
Rigid mechanisms lag during shocks, invite reflexive selloffs, and can amplify stress. Filtering oracle noise and delayed parameter changes worsen outcomes.
AI augments these designs by forecasting volatility, tuning parameters before stress widens, and rebalancing collateral mixes based on real-time market conditions. With filtered oracle inputs, systems can select liquidation thresholds and rebalance reserves to improve overall stability.
- Trade-offs: decentralization vs. capital efficiency vs. robustness.
- Foundational choices set data needs, architecture, and governance limits.
- Next: how the stack implements these economic mechanisms on-chain and off-chain.
machine learning cryptocurrency algorithmic stablecoin protocols
Defining the stack: design starts by mapping how market signals become on-chain actions. A resilient stack links contracts for mint/burn and vaults with off-chain model servers, oracle feeds, and governance dashboards.
Data, models, mechanisms, and governance
Data ingestion normalizes price feeds, venue depth, oracle health, and sentiment. Feature stores feed lightweight models that forecast short-term moves and flag anomalies.
- Interfaces: REST or gRPC APIs connect model outputs to mint/burn contracts and collateral vaults.
- Mechanisms: rebases, fees, and incentives accept parameter updates from verified analytics.
- Governance: dashboards and explainable outputs make changes auditable and traceable.
Embed risk controls at every layer: rate limits, caps, circuit breakers, and manual kill switches with community oversight. Deploy experiments in isolated environments so development and live systems stay separate while enabling safe upgrades and rapid analysis of new policies.
System Architecture Blueprint for an AI-Enhanced Stablecoin
Below is a compact architecture map showing how on-chain modules and off-chain analytics interact. The goal is a resilient, auditable system that keeps the peg predictable while limiting operational blast radius.
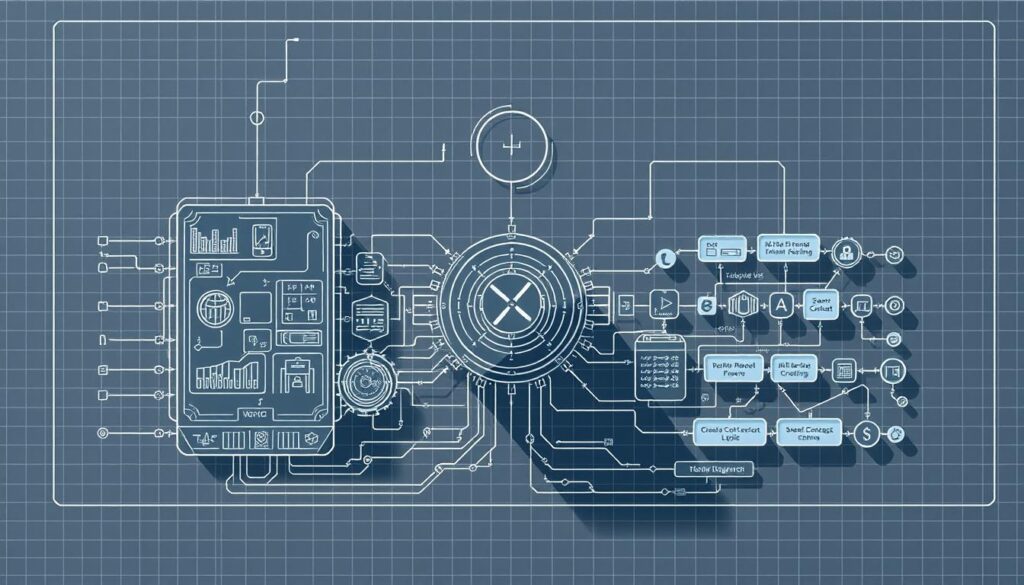
On-chain components
Core modules: token contract, mint/burn controller, collateral vaults, fee routers, and emergency pause capabilities. These contracts enforce guardrails for supply changes and liquidation limits.
Off-chain intelligence
Low-latency model servers host forecasting and policy agents. Feature stores and data pipelines feed observability tools with alerting SLAs for rapid response.
Oracle layer and redundancy
Aggregate multiple providers, medianize feeds, reject outliers, and require heartbeat checks. Use multi-oracle strategies and geo-distributed RPC endpoints to remove single points of failure.
Security perimeter and safe upgrades
Detect unusual order flow, oracle deviations, and liquidity imbalances with pattern-based alerts. Apply automated throttles, rate limits, and pausable modules to stop cascade events.
- Separate deployment boundaries: minimal trust between contracts and off-chain services.
- Collateral vaults expose risk parameters to models but enforce limits on-chain.
- Safe upgrades use proxy patterns, timelocks, and staged rollouts tied to monitoring thresholds.
Outcome: an operational design focused on resilience, predictable performance, and defensible peg maintenance across market regimes.
Data Strategy: Market Conditions, Oracles, and Real-Time Feeds
Successful peg defense starts with a data plan that ties real-time feeds to clear policy levers. Good inputs let teams act before stress becomes a crisis. The focus is on high-signal features, reliable oracles, and clear escalation paths.
On-chain signals and cross-chain flows
Track pool depths, slippage curves, funding rates, and bridge flows. These features show liquidity stress and sudden shifts in market conditions. Use rolling windows and regime flags to spot volatility clusters.
Off-chain context and demand signals
Ingest macro releases, news embeddings, and social sentiment time series. Combine order flow and venue spreads to anticipate demand shocks and adjust reserves or fees.
Oracle reliability and data quality
Design multi-source aggregation with staleness checks and outlier filters. Add signed provenance, schema validation, deduplication, and latency SLOs to reduce risk from bad prints.
- Backfill and replay historical feeds to validate policy changes.
- Map signals to levers: collateral ratios, fees, and mint/burn rates.
- Use fallbacks, confidence intervals, and circuit breakers for outage resilience.
| Signal | Why it matters | Typical action |
|---|---|---|
| Pool depth | Shows liquidity available at best prices | Tighten fees; increase reserves |
| Funding & spreads | Indicates leverage and cross-venue stress | Limit minting; trigger alerts |
| News & sentiment | Signals demand shocks before on-chain moves | Adjust incentives; preemptive rebalancing |
| Oracle health | Prevents manipulation and stale prices | Switch source or pause policy changes |
Model Selection and Training for Price Stability
Choose forecasting and control approaches that match your peg goals, data latency, and governance speed.
Forecasting toolset: sequence models like LSTM, tree ensembles such as gradient boosting (GBM), and transformers each suit different signal mixes. LSTMs work well for compact time series. GBMs handle tabular, cross-venue features. Transformers scale for multi-signal, high-frequency inputs.
Reinforcement agents tune policy levers in simulated markets. Agents learn to adjust supply, fees, and incentives under constraints. Reward functions penalize peg deviation, long recovery times, and excessive supply volatility.
Backtesting must use walk-forward validation to avoid leakage. Agent-based simulations should include adversarial actors and oracle drift to test manipulation resistance. Stress scenarios to run: flash crashes, liquidity evaporation, correlated reserve drawdowns, and cross-chain fragmentation.

Evaluation and Risk Controls
- Performance metrics: forecast error, policy regret, reserve drawdown, and time-to-recover the peg.
- Model risk: require explainability, versioning, canary deployments, and fast rollback paths.
- Operational tie-in: match decision latency to safe on-chain actuation and governance review windows.
| Component | Primary benefit | Key test |
|---|---|---|
| LSTM | Short-term sequence forecasting | One-step ahead RMSE on venue prices |
| Gradient boosting | Robust tabular signals and feature importance | Out-of-sample MAE with walk-forward validation |
| Transformers | Multi-signal, long-range context | Multi-horizon accuracy and latency profiling |
| Reinforcement agent | Adaptive policy under simulated stress | Policy regret and recovery time across adversarial sims |
Stability Mechanisms: Supply, Incentives, and Collateral Management
A robust stability stack ties mint/burn actions, fee design, and collateral policies to short-term market signals. Systems must act quickly when demand shifts or liquidity thins. Clear levers and visible rules help users react predictably.
Dynamic supply tools
Menu: elastic rebase, direct mint/burn, and multi-token seigniorage share systems. Rebase adjusts token supply across holders to nudge price. Mint/burn lets the protocol expand or shrink supply against collateral.
Incentive design
Fees, bonding discounts, and LP rewards steer behavior. Bonding can encourage buys when the peg dips. Fee ramps and LP boosts align market makers to keep order books deep and orderly.
AI-optimized collateral ratios & liquidation protection
AI monitors volume, price moves, and sentiment to tune collateral levels in near real time. Models raise buffers before forecasted volatility to reduce liquidation cascades.
Liquidation protection uses staged auctions, backstop liquidity, and dynamic penalties. These steps discourage opportunistic attacks and slow down cascading sales.
- Map signals to levers: predicted demand or liquidity shortfalls trigger fee changes and supply throttles.
- Rate limits and guardrails prevent overreaction when inputs are noisy.
- Simulate interactions to catch feedback loops before mainnet launches.
| Lever | Primary trigger | Typical action | Measured outcome |
|---|---|---|---|
| Rebase | Persistent peg drift | Adjust token supply across holders | Peg deviation reduction |
| Mint/Burn | Collateral shortfall or surplus | Mint for demand; burn to reduce supply | Recovery time |
| Fees & Penalties | Low depth / high spreads | Raise fees; apply dynamic penalties | Order book depth |
| Collateral tuning | Predicted volatility spike | Increase reserve ratios | Lower liquidation rate |
Transparency matters. Publish parameter changes and model rationales so users and market makers trust interventions. Tie each mechanism to metrics like peg deviation and recovery time to prove effectiveness.
Governance and Transparency in AI-Driven Protocols
Effective policy design gives tokenholders the final say while letting analytics surface timely proposals. This balance keeps decisions grounded in data and aligned with community priorities.

Decentralized governance augmented by analytics
Design a framework where on-chain votes ratify changes that analytics propose. Let systems produce explainable summaries so tokenholders can judge risks and benefits quickly.
Auditability: explainable AI outputs and parameter logs
Publish immutable records for every model version, training window, and parameter diff tied to contracts and votes. Make activation timestamps and datasets auditable so auditors and developers can replay decisions.
- Require clear role definitions and time-limited emergency councils with community veto power.
- Integrate real-time dashboards showing peg deviation, oracle health, and liquidity conditions before votes.
- Mandate third-party audits, red-team reviews, and public postmortems for significant incidents.
- Provide plain-language summaries for users and technical appendices for auditors to aid transparency.
- Align incentives for cautious development via staking, slashing, and quorum thresholds to reduce rushed upgrades.
Outcome: governance treated as part of protocol security and stability, not an afterthought, helps meet regulatory and trust challenges while keeping systems accountable.
Security, Risk Management, and De-Peg Defense
Protecting a peg requires layered systems that mix automated detection with clear human runbooks. This section outlines threat surfaces, live defenses, and liquidity playbooks to keep markets stable.
Threat models: flash loans, oracle games, manipulation
Common attack surfaces include oracle spoofing, sandwiching around updates, liquidity drains, and flash-loan cascades on cross-chain networks. Map exposures by venue and asset to cap concentration risk.
Real-time anomaly detection and circuit breakers
AI and lightweight algorithms flag spikes in spreads, depth divergence, and oracle drift. High anomaly scores trigger rate limits, temporary halts to mint/burn, fee escalators, or alternative oracle routes.
Liquidity management across volatile regimes
Maintain pre-positioned backstops, RFQ lanes, and conditional incentives to attract stabilizing flow when supply or depth drops. Integrate on-chain intel with off-chain sentiment for early warning.
- Runbooks: severity tiers, comms, parameter overrides, and post-incident audits.
- Testing: adversarial sims, oracle outages, and correlated collateral selloffs.
- Forensics: robust logging for remediation and reporting.
| Defense | Trigger | Action | Metric |
|---|---|---|---|
| Oracle redundancy | Feed deviation | Switch sources; pause updates | Oracle integrity score |
| Circuit breaker | Depth loss / spread spike | Halt mint/burn; raise fees | Mean time to containment |
| Liquidity backstop | Rapid outflow | RFQ auction; incentive boosts | Recovery time to peg |
Continuous improvement is essential. Update thresholds, models, and playbooks as attackers evolve so stablecoins remain resilient under stress.
Regulatory and Compliance Considerations in the United States
U.S. teams building pegged digital assets must align product choices with federal compliance obligations early in development. Good design keeps users safe and markets fair while reducing legal risk.

KYC/AML workflows compatible with DeFi rails
Optional gateways let vetted participants access permissioned features without fragmenting open liquidity. Gateways can sit at fiat on-ramps, custodial bridges, or optional mint/burn endpoints.
AI aids detection by flagging anomalous patterns while preserving privacy through thresholding and human review. Sanctions screening and travel-rule messaging are added where required.
Audit trails for AI decisions and policy changes
Keep versioned models, signed parameter change logs, and recorded governance votes. Timelocks and on-chain records make upgrades auditable and enforceable.
- Define entity responsibilities for U.S. users, disclosures, and incident reporting.
- Publish reserve snapshots and timely disclosures to support market integrity and price confidence.
- Map compliance tech to operational controls so legal duties are technical controls.
| Area | Control | Outcome |
|---|---|---|
| KYC/AML | Permissioned gateway + AI screening | Compliant access without breaking interoperability |
| Auditability | Versioned models, parameter logs, timelocks | Clear records for regulators and auditors |
| Market integrity | Public reserve data & disclosure cadence | Trust in price and reported value |
Build Plan: From Prototype to Mainnet Deployment
Begin your rollout with a focused prototype that proves core integrations and safety checks under controlled stress. Start by wiring oracles, a simple supply rule, and a lightweight forecasting model to validate plumbing and actuation paths.
Testnet experiments and agent-based simulations
Use a backtesting pipeline with walk-forward evaluation and scenario libraries for extreme price moves and oracle outages. Run agent-based sims that include adversaries to stress-test manipulation resistance and liquidity shocks.
Canary releases, monitoring SLAs, and incident response
Stage deployments across devnet, public testnet, and a guarded mainnet with canary contracts. Define observability: uptime targets, peg-deviation alerts, and response SLOs.
- Incident playbooks: roles, temporary overrides, and pause criteria.
- Upgrade paths: proxy patterns, timelocks, and predictable release cadence.
- Change management: versioned models, rollback plans, and auto-reversion on metric regressions.
- Align validators, oracles, and partners on readiness checks and document each stage for auditors and community review.
Costs, Resourcing, and Economic Sustainability
A durable economic design begins with honest budgeting for models, data pipelines, and security reviews. Early cost estimates shape how teams staff R&D, select vendors, and size contingency reserves.
Model R&D, data integration, and smart contract audits
Plan line items for data engineering, experiment cycles, and oracle integrations. Add fees for contract audits, formal verification, and recurring penetration tests.
Account for ongoing spend: model retraining, monitoring stacks, incident drills, and a live bug bounty program. These reduce technical risk and protect users.
Treasury design: yield strategies to support the peg
Design a treasury policy that prioritizes liquidity and safety, not just nominal yield. Use low-risk DeFi lanes, short-duration assets, and diversified custody to protect reserves and operational runway.
- Vendor vs. in-house: trade costs, control, and SLAs.
- KPIs: peg variance, recovery time, and lower tail exposure.
- Maintain contingency funds and insurance for black swans.
| Cost Center | Typical annual | Outcome |
|---|---|---|
| Data & models | $250k–$800k | Faster response to market shifts |
| Audits & security | $100k–$400k | Lower exploit risk |
| Treasury operations | $50k–$200k | Safe assets and liquidity |
Link spending to measurable outcomes: tighter peg, quicker recovery, and preserved value and price confidence for users of stablecoins. Sustainable funding keeps the project resilient and credible in the U.S. market.
Case Studies and What They Teach Builders Now
Real-world examples show which guardrails worked and which amplified peg failures under pressure.
DAI and FRAX: hybrid lessons
DAI uses diversified collateral and advanced risk scoring to limit shocks. Teams now add AI-assisted risk signals for collateral limits and liquidation paths.
FRAX blends reserves with supply rules and tunes collateral ratios dynamically. Its model shows how data-driven ratio shifts improve recovery without sacrificing liquidity.
Ampleforth and Curve: supply and fee mechanisms
Ampleforth’s elastic supply targets purchasing power through automated expansions and contractions. Modern projects augment these mechanisms with predictive models to reduce blunt supply swings.
Curve applies dynamic fee optimization and incentive allocation to deepen markets. AI-informed fee curves help keep spreads tight and reduce volatility for stable assets.
Terra/UST: failure modes and guardrails
Terra exposed how confidence spirals and reflexive mint/burn can cause hyperinflation and rapid de-pegging. Key failures: single-design reliance and weak circuit breakers.
Lessons: anomaly-filtered oracles, RL-informed policies, and staged auctions could have slowed feedback loops and limited contagion.
- Measure peg deviation, liquidity depth, and recovery time for real insight.
- Prefer diversified backing and on-chain limits to blunt reflexive spirals.
- Use AI to augment risk signals, not to replace conservative economic design.
| Case | Key mechanism | What worked | Design takeaway |
|---|---|---|---|
| DAI | Hybrid collateral + risk scoring | Resilience from diversified backing | AI risk signals for collateral limits |
| FRAX | Dynamic collateral ratio | Faster peg recovery with conservative shifts | Tune ratios with transparent triggers |
| Ampleforth | Elastic supply | Purchasing-power targeting | Use predictive models to smooth rebase |
| Curve | Dynamic fees & incentives | Improved depth and lower spreads | AI-driven fee curves with audit logs |
| Terra/UST | Reflexive mint/burn | Rapid collapse under confidence loss | Implement circuit breakers and reserve diversity |
Postmortem template: log timelines, model versions, oracle health, governance votes, and measured outcomes. Convert incidents to fixed checks, updated runbooks, and scheduled audits to improve long-term stability.
Metrics That Matter: Proving Stability and Trust
Metrics that teams publish guide how quickly markets regain trust after a shock. Clear, consistent signals let governance and operators act before a small drift becomes a crisis.
Peg deviation, recovery time, and liquidity depth
Track peg bands and define alert tiers for minor, moderate, and severe drift. Publish time-to-recover for each incident so stakeholders see how interventions perform.
Measure liquidity at top-of-book across major venues to assess market resilience and to tune fee ramps or incentives.
Oracle integrity score and manipulation detection rate
Score feeds by freshness, variance across sources, and anomaly detection true/false positives. A high integrity score reduces the chance of bad prints driving on-chain actions.
Operational metrics to publish:
- Forecast error, policy regret, and intervention efficiency during live events.
- User trust proxies: active addresses, retention, and on-chain payment share.
- Cost of stability: fees, incentives, and collateral opportunity cost.
| Metric | Why it matters | Action threshold |
|---|---|---|
| Peg deviation (%) | Shows loss of peg confidence | Alert at 0.5%, 1.5%, 3% |
| Recovery time (min) | Measures intervention speed | Target < 60 minutes |
| Top-book liquidity ($) | Indicates market depth | Maintain minimum across venues |
| Oracle integrity score | Signals feed health | Pause on score drop < 0.7 |
Publish dashboards and parameter logs, link metrics to governance triggers, and benchmark against peers to prioritize system investments and keep value stable for users in the U.S. market.
Where AI-Powered Stablecoins Are Heading Next
Where AI-Powered Stablecoins Are Heading Next
Future stable assets will act as self-stabilizing agents that both defend pegs and fund ongoing development. Expect AI-native treasuries that allocate to low-risk strategies to earn yield while they help maintain stable supply and reserves.
Protocols will weave tighter integrations across the DeFi ecosystem so fees and incentives adjust by venue. Oracle stacks will use ensemble feeds and signed data to deter manipulation at scale.
Governance will demand public model cards, changelogs, and test results for auditability. Reinforcement methods will tune monetary responses as markets shift. The path forward favors measured rollouts, rigorous metrics, and open collaboration across the U.S. ecosystem.


No comments yet