The world of cryptocurrency is a fascinating and rapidly evolving landscape, where the signing of a digital signature by a crypto wallet marks the beginning of a complex and intricate transaction process. In this article, we’ll delve into the inner workings of the crypto transaction process, exploring the critical steps that occur after a wallet signs a signature, from digital signature verification to the updates on the decentralized blockchain network.
At the heart of the crypto ecosystem lies the wallet software, which serves as the gateway for users to manage their digital assets. The functionality of these wallets extends far beyond mere storage; they play a crucial role in the entire transaction lifecycle, from securely storing cryptographic keys to facilitating seamless peer-to-peer network interactions.
Alongside the wallet software, the management of cryptographic keys is a fundamental aspect of the cryptocurrency landscape. Understanding the importance of private key security measures and the transparency of public keys is essential in ensuring the overall security and integrity of the system.
As we navigate through the complexities of the crypto world, we’ll also uncover the intricacies of the decentralized ledger updates, shedding light on the various consensus mechanisms that power the blockchain network.
By exploring the anatomy of a digital signature and the dynamic peer-to-peer network dynamics, we’ll gain a comprehensive understanding of the end-to-end crypto transaction flow, from the initial wallet signature to the final updates on the distributed ledger.
Join us as we embark on this journey, uncovering the hidden mechanics that drive the cryptocurrency ecosystem and the crucial role of the crypto wallet in this captivating digital landscape.
Key Takeaways
- Understand the critical steps involved in the crypto transaction process after a wallet signs a digital signature.
- Explore the functionality and inner workings of cryptocurrency wallet software.
- Discover the importance of cryptographic key management in ensuring the security and integrity of the crypto ecosystem.
- Delve into the decentralized ledger updates and the various consensus mechanisms that power the blockchain network.
- Gain insights into the dynamic peer-to-peer network interactions and the end-to-end crypto transaction flow.
Crypto Transaction Process Demystified
When a cryptocurrency wallet signs a digital signature, the transaction process is set in motion. This critical step ensures the authenticity and integrity of the transaction before it is broadcasted to the decentralized network. Understanding the intricacies of digital signature verification and peer-to-peer network broadcasting is essential for navigating the world of cryptocurrency transactions.
Digital Signature Verification
The digital signature verification process is the first step in validating a cryptocurrency transaction. This cryptographic method verifies the sender’s identity and confirms that the transaction data has not been tampered with. By leveraging advanced algorithms, the network nodes can reliably authenticate the digital signature, establishing trust and security in the overall transaction process.
Peer-to-Peer Network Broadcasting
Once the digital signature is verified, the signed transaction is broadcasted across the peer-to-peer network. This distributed network of nodes works collaboratively to validate the transaction and incorporate it into the decentralized ledger. This process ensures that the transaction is widely acknowledged and recorded in a transparent and tamper-resistant manner, providing a secure and immutable record of the cryptocurrency movement.
Mastering the intricacies of the crypto transaction process, from digital signature verification to peer-to-peer network broadcasting, is crucial for understanding the security and resilience of cryptocurrency transactions in the digital age.
Wallet Software Functionality Unveiled
Crypto wallets play a crucial role in the digital asset ecosystem, providing users with secure storage and management of their cryptographic keys. Understanding the underlying wallet software functionality is essential for navigating the entire transaction process. These software applications serve as the gateway between users and their cryptocurrencies, facilitating the secure transfer of digital assets.
At the core of wallet software functionality lies the cryptographic key management system. Wallets generate and store private and public keys, which are the unique identifiers used to access and control cryptocurrency funds. This robust key management system ensures the security of users’ digital assets, protecting them from unauthorized access and theft.
Wallets also offer a wide range of features that enhance the user experience and facilitate seamless cryptocurrency transactions. These may include transaction history tracking, exchange integration, and multi-currency. Additionally, advanced wallet software can integrate with smart contract technologies, expanding their functionality beyond simple asset custody.
“Crypto wallets are the foundation of the digital asset ecosystem, providing users with the tools to securely manage and control their wealth in the decentralized web.”
As the cryptocurrency landscape continues to evolve, the functionality of wallet software is also advancing. From enhanced security measures to innovative features, these applications play a crucial role in empowering users to take charge of their digital assets and navigate the exciting world of Web3.
Cryptographic Key Management Essentials
Cryptocurrency wallets rely on robust cryptographic techniques to safeguard user funds. At the heart of this security infrastructure lie cryptographic key management practices that ensure the confidentiality and integrity of digital assets. Understanding the fundamental principles of this process is crucial for maintaining the overall cryptocurrency wallet security.
Private Key Security Measures
The private key is the primary access credential that grants users control over their digital assets. Securing this key is of the utmost importance, as a compromised private key can lead to the loss or theft of the associated funds. Effective private key security measures include:
- Storing private keys in offline, hardware-based wallets (also known as “cold storage”)
- Implementing strong password protection and two-factor authentication
- Regularly backing up private keys to prevent data loss
- Educating users on the importance of private key management
Public Key Transparency
In contrast to private keys, public keys are designed to facilitate transparent transactions within the cryptocurrency network. Public keys are derived from private keys and are used to receive digital assets. By ensuring public key transparency, the network can verify the authenticity of transactions and prevent double-spending attempts. This transparency is achieved through:
- Decentralized public ledgers, such as blockchain, that record all transactions
- Cryptographic algorithms that enable the verification of public keys without compromising privacy
- Ongoing monitoring and auditing of the network to detect any irregularities

“Effective cryptographic key management is the foundation of secure cryptocurrency wallets, ensuring the protection of user funds and the integrity of the entire network.”
What Happens After Crypto Wallet Signs Signature
In the world of cryptocurrency, the process that unfolds after a crypto wallet signs a digital signature is a crucial step in the transaction lifecycle. This signature, a cryptographic proof of the wallet owner’s authorization, sets the crypto transaction process in motion, leading to a series of critical events that ultimately update the decentralized blockchain network.
Once the crypto wallet has signed the digital signature, the transaction is ready for verification. This verification process involves the crypto transaction process, where the signed transaction data is scrutinized by the peer-to-peer network to ensure its validity and compliance with the network’s rules. Digital signature verification plays a pivotal role in this stage, ensuring that the transaction was indeed authorized by the legitimate wallet owner.
After the transaction is successfully verified, it is then broadcasted to the entire peer-to-peer network, where other nodes (computers or devices participating in the network) receive and validate the transaction. This decentralized broadcasting ensures that the transaction information is propagated throughout the network, preparing it for the final stage of integration into the blockchain.
The final step in the process is the incorporation of the verified transaction into the decentralized blockchain network, which updates the public ledger and reflects the changes in the wallet’s balance. This update to the blockchain, a distributed digital record of all transactions, is a critical milestone in the crypto transaction lifecycle, serving as a permanent and tamper-proof record of the wallet’s financial activity.
“The integration of the verified transaction into the decentralized blockchain network is a defining moment in the crypto transaction process, solidifying the changes in the wallet’s balance and contributing to the overall integrity of the distributed digital ledger.”
Decentralized Ledger Updates Explained
The blockchain, a decentralized ledger technology, requires a collaborative effort to maintain the integrity of the public record. This is achieved through the implementation of consensus mechanisms, which play a crucial role in validating transactions and updating the blockchain in a secure and transparent manner.
Consensus Mechanisms Explored
Two prominent consensus mechanisms used in blockchain networks are Proof of Work and Proof of Stake. Proof of Work relies on a competition among network participants, known as miners, to solve complex mathematical problems to validate transactions and add new blocks to the blockchain. In contrast, Proof of Stake assigns validation rights based on the amount of cryptocurrency held by network participants, known as validators.
“Consensus mechanisms ensure that the decentralized ledger is updated in a secure and transparent way, preserving the integrity of the blockchain network.”
These consensus mechanisms play a crucial role in maintaining the decentralized ledger updates and ensuring the overall blockchain transaction flow remains secure and reliable. By reaching a consensus on the validity of transactions, the blockchain network can effectively update the shared ledger without the need for a centralized authority.
Blockchain Transaction Flow Visualized
The journey of a cryptocurrency transaction can be visualized as it passes through the various stages of the blockchain network. From the initial signing of the digital signature to the final update of the distributed ledger, each step plays a crucial role in the overall blockchain transaction flow.
At the heart of the crypto transaction process lies the digital signature, which authenticates the sender’s identity and authorizes the transfer of funds. Once the signature is verified, the transaction is broadcasted to the peer-to-peer network, where it is validated by the network nodes.
As the transaction progresses, the decentralized ledger updates are meticulously recorded, ensuring the transparency and immutability of the blockchain. This process is governed by the network’s consensus mechanism, which ensures that all participants agree on the validity of the transaction before it is permanently added to the distributed ledger.
“The blockchain transaction flow is a fascinating interplay of cryptography, peer-to-peer networking, and distributed consensus, all working together to facilitate secure and transparent digital transactions.”
By visualizing the various stages of the blockchain transaction flow, we can gain a deeper understanding of the intricate workings of this revolutionary technology. From the initial wallet interaction to the final ledger update, each step plays a crucial role in ensuring the integrity and reliability of the crypto transaction process.
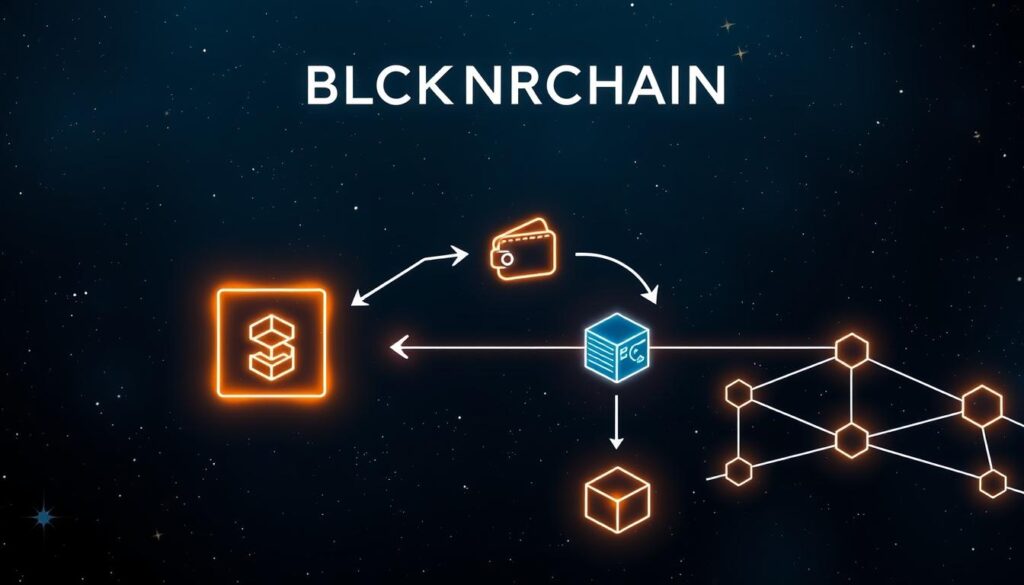
As we continue to explore the blockchain ecosystem, it’s important to appreciate the ingenuity and complexity that underpins the blockchain transaction flow. This understanding will not only deepen our appreciation for the technology but also help us navigate the evolving world of digital finance and decentralized applications.
Cryptocurrency Wallet Security Protocols
Securing your cryptocurrency holdings is of paramount importance in the digital asset ecosystem. Crypto wallets employ a range of security protocols to safeguard user funds from various threats. Understanding these protocols is crucial for anyone venturing into the world of cryptocurrency wallet security.
Cold Storage Solutions
One of the most effective ways to protect your digital assets is through cold storage solutions, such as hardware wallets. These devices keep your private keys offline, making them virtually immune to online attacks. By physically disconnecting your cryptographic keys from the internet, you can significantly reduce the risk of unauthorized access and theft.
Hot Wallet Risks
In contrast, hot wallets are digital wallets connected to the internet, offering greater convenience but also presenting inherent hot wallet risks. These wallets are susceptible to various cyber threats, such as hacking, phishing, and malware attacks. While hot wallets can be useful for day-to-day transactions, it is essential to carefully manage the cryptographic key management and maintain robust security protocols to mitigate the risks.
Striking the right balance between the security of cold storage and the accessibility of hot wallets is a crucial consideration in the world of cryptocurrency. By understanding the various security protocols and their implications, users can make informed decisions to protect their digital assets effectively.
Anatomy of a Digital Signature
At the heart of the crypto transaction process lies the digital signature, a secure and tamper-proof proof of ownership. Understanding the inner workings of digital signatures, including the role of cryptographic key management, is essential for navigating the cryptocurrency ecosystem.
A digital signature is created using a private key, a unique cryptographic code that serves as a digital equivalent of a handwritten signature. This private key is paired with a public key, which is used to verify the authenticity of the signature. When a user initiates a cryptocurrency transaction, their digital wallet signs the transaction with their private key, creating a unique digital signature.
- The digital signature is then broadcast to the peer-to-peer network, where other nodes verify the signature using the signer’s public key.
- This verification process ensures that the transaction was indeed initiated by the rightful owner of the funds and has not been tampered with.
- Once the signature is validated, the transaction is added to the decentralized ledger, known as the blockchain, and the transfer of cryptocurrency is complete.
The seamless integration of digital signatures into the crypto transaction process is a testament to the advanced cryptographic key management techniques employed in the cryptocurrency ecosystem. This robust security mechanism safeguards the integrity of digital assets and fosters trust in the decentralized financial system.
“The digital signature is the cornerstone of secure cryptocurrency transactions, ensuring the uncompromised transfer of digital assets.”
Peer-to-Peer Network Dynamics
Cryptocurrency networks rely on a decentralized, peer-to-peer architecture, where nodes work together to validate transactions and maintain the integrity of the blockchain. This unique structure is essential for the reliable and secure flow of data within the network.
Node Synchronization Strategies
Effective node synchronization strategies are crucial for ensuring the seamless blockchain transaction flow. Nodes in a peer-to-peer network must constantly communicate and update each other to maintain a unified view of the blockchain. This process, known as node synchronization, involves several key techniques:
- Periodic block and transaction exchange: Nodes regularly share the latest blocks and transactions they have validated, allowing the entire network to stay synchronized.
- Gossip protocols: Nodes use gossip-based algorithms to quickly propagate information about new blocks and transactions throughout the network.
- Consensus mechanisms: The network employs consensus protocols, such as Proof-of-Work or Proof-of-Stake, to ensure that all nodes agree on the valid state of the blockchain.
By implementing robust node synchronization strategies, cryptocurrency networks can ensure that the peer-to-peer network remains cohesive and resilient, supporting the seamless flow of blockchain transactions.

“Effective node synchronization is the backbone of a secure and efficient cryptocurrency network, enabling the reliable exchange of transactions and maintaining the blockchain’s integrity.”
Wallet Software Development Lifecycle
The development and evolution of crypto wallet software is a critical aspect of the digital asset ecosystem. From initial design and cryptographic key management considerations to ongoing maintenance and updates, the wallet software functionality lifecycle plays a pivotal role in providing users with a secure and reliable platform for managing their digital assets.
The wallet software development lifecycle encompasses several key stages:
- Requirement gathering: Identifying user needs, security requirements, and regulatory compliance guidelines.
- Cryptocurrency wallet security implementation: Integrating robust security measures, such as multi-factor authentication, biometric authentication, and secure storage of private keys.
- User interface design: Creating a intuitive and user-friendly interface that enhances the overall user experience.
- Deployment and testing: Rigorous testing to ensure the wallet software’s functionality, reliability, and scalability.
- Continuous maintenance and updates: Addressing bug fixes, implementing new features, and staying current with industry best practices.
“The security and reliability of a cryptocurrency wallet is paramount, as it serves as the gateway to managing digital assets.”
Throughout the development lifecycle, wallet software providers must prioritize user privacy, cryptographic key management, and overall wallet software functionality to build a trusted and secure platform for their customers. By adopting a comprehensive approach to wallet software development, organizations can stay ahead of the curve and meet the evolving needs of the cryptocurrency ecosystem.
Regulatory Compliance Considerations
As the cryptocurrency industry continues to evolve, adhering to regulatory frameworks, such as Know Your Customer (KYC) and Anti-Money Laundering (AML) guidelines, has become increasingly vital for cryptocurrency wallet providers. These compliance measures are essential in ensuring the integrity and legitimacy of crypto platforms, safeguarding users and the industry as a whole.
KYC and AML Guidelines
Cryptocurrency wallet providers must navigate the complex regulatory landscape to implement robust KYC and AML protocols. These guidelines require wallet providers to verify the identity of their users, monitor transactions for suspicious activity, and report potential instances of financial crimes to the appropriate authorities. Compliance with these regulations is crucial in mitigating the risks of cryptocurrency wallet security breaches and illicit activities.
Crypto wallet providers must ensure that their platforms adhere to the following KYC and AML best practices:
- Implement robust user identification and verification measures
- Continually monitor transactions for suspicious patterns
- Establish clear policies and procedures for reporting potential financial crimes
- Regularly review and update their regulatory compliance practices to keep pace with evolving industry standards
By prioritizing KYC and AML guidelines, cryptocurrency wallet providers can build trust, protect their users, and contribute to the overall regulatory compliance and stability of the cryptocurrency ecosystem.
Emerging Trends in Wallet Technology
The world of cryptocurrency is constantly evolving, and the crypto wallet technology is no exception. From advancements in wallet software functionality to enhanced cryptocurrency wallet security protocols, the landscape of digital asset management is transforming rapidly.
One of the exciting trends in the crypto wallet space is the rise of multi-signature wallets. These innovative solutions require multiple keys to authorize a transaction, significantly bolstering blockchain transaction flow security and reducing the risk of unauthorized access.
Another emerging trend is the integration of decentralized finance (DeFi) protocols within crypto wallets. This integration allows users to seamlessly access a wide range of DeFi services, such as lending, borrowing, and yield farming, all within the comfort of their trusted wallet interface.
As the crypto industry continues to mature, we can expect to see even more advancements in wallet software functionality, cryptocurrency wallet security measures, and the integration of cutting-edge technologies like quantum-resistant encryption and biometric authentication.
“The evolution of crypto wallets is a critical component in the broader adoption and utilization of digital assets. As the technology continues to advance, users can look forward to an increasingly secure, user-friendly, and feature-rich experience.”
By staying at the forefront of these emerging trends, cryptocurrency holders can ensure the safety and efficacy of their digital asset management, paving the way for a more secure and seamless blockchain transaction flow.
Cross-Chain Interoperability Challenges
As the cryptocurrency ecosystem continues to expand, the ability to seamlessly transfer digital assets across different blockchain networks has become a crucial challenge. Addressing the cross-chain interoperability issues is essential for unlocking the full potential of the decentralized finance (DeFi) landscape.
The blockchain transaction flow, decentralized ledger updates, and peer-to-peer network broadcasting across various blockchain platforms often face compatibility and integration obstacles. This fragmentation can hinder the free movement of cryptocurrencies, tokens, and other digital assets, limiting the overall utility and growth of the crypto industry.
To overcome these challenges, developers and researchers are exploring innovative solutions, such as:
- Interoperability protocols that enable seamless communication and asset transfers between different blockchain networks
- Decentralized exchanges (DEXs) that facilitate cross-chain swaps and liquidity sharing
- Blockchain bridges that connect disparate blockchain ecosystems, allowing for the movement of assets and data
By addressing the cross-chain interoperability challenges, the cryptocurrency industry can unlock new opportunities for collaboration, innovation, and the creation of a more interconnected, inclusive, and efficient decentralized financial system.
“The ability to move value and information seamlessly across different blockchains is crucial for the widespread adoption and growth of the cryptocurrency industry.”
Scalability Solutions for Blockchain Networks
As the adoption of cryptocurrencies and blockchain technology grows, the need for scalable solutions to handle the increasing volume of transactions has become paramount. Innovations in layer-2 protocols, sharding, and other scaling techniques are being explored to ensure the long-term viability and efficiency of blockchain networks.
One prominent solution is the development of layer-2 protocols, which operate on top of the base blockchain and enable faster and more cost-effective transactions. These protocols, such as the Lightning Network for Bitcoin or the Polygon network for Ethereum, facilitate off-chain transactions and then periodically settle them on the main blockchain, reducing the burden on the decentralized ledger and enhancing the overall blockchain transaction flow.
Another approach to scalability is sharding, which involves dividing the blockchain network into smaller, more manageable partitions called “shards.” Each shard processes a subset of transactions, allowing for parallel processing and increased throughput. This technique helps address the challenges associated with decentralized ledger updates and peer-to-peer network broadcasting, improving the overall scalability of the blockchain system.
FAQ
What happens after a crypto wallet signs a digital signature?
Once a crypto wallet signs a digital signature, the transaction is set in motion. The signed transaction is then verified, broadcasted across the peer-to-peer network, and ultimately incorporated into the decentralized blockchain, updating the public ledger and reflecting the changes in the wallet’s balance.
How does the crypto transaction process work?
The crypto transaction process involves several key steps: 1) Digital Signature Verification – The signed transaction is verified to ensure the authenticity of the transaction. 2) Peer-to-Peer Network Broadcasting – The signed transaction is broadcasted across the peer-to-peer network, where nodes work to validate and incorporate it into the decentralized ledger.
What are the key functionalities of crypto wallet software?
Crypto wallets provide users with secure storage and management of their private and public cryptographic keys, which are essential for accessing and transacting digital assets. Understanding the underlying functionality of wallet software is crucial to comprehending the entire cryptocurrency transaction process.
How do cryptographic key management techniques ensure wallet security?
Crypto wallets rely on advanced cryptographic techniques to secure user funds. Private keys, which grant access to digital assets, require robust security measures to prevent unauthorized access. Meanwhile, public keys facilitate transparent transactions within the network.
How are decentralized ledger updates processed on the blockchain network?
The decentralized nature of blockchain networks requires a collaborative effort to maintain the integrity of the public ledger. Consensus mechanisms, such as Proof of Work or Proof of Stake, are employed to validate transactions and update the blockchain in a secure and transparent manner.
What are the key steps in the blockchain transaction flow?
The journey of a cryptocurrency transaction can be visualized as it passes through the various stages of the blockchain network. From the initial signing of the digital signature to the final update of the distributed ledger, each step plays a crucial role in the overall transaction flow.
What security protocols do crypto wallets employ to protect user funds?
Crypto wallets employ a range of security protocols to safeguard user funds. Cold storage solutions, such as hardware wallets, offer enhanced security by keeping private keys offline, while hot wallets connected to the internet present certain risks that must be carefully managed.
How do digital signatures work in the context of cryptocurrency transactions?
At the heart of a cryptocurrency transaction lies the digital signature, which serves as a secure and tamper-proof proof of ownership. Understanding the inner workings of digital signatures, including the role of private and public keys, is essential for navigating the crypto ecosystem.
How do peer-to-peer network dynamics impact the cryptocurrency ecosystem?
Cryptocurrency networks rely on a decentralized, peer-to-peer architecture, where nodes work together to validate transactions and maintain the integrity of the blockchain. Effective node synchronization strategies are crucial for ensuring the seamless flow of information within the network.
What are the key considerations in the wallet software development lifecycle?
The development and evolution of crypto wallet software is a critical aspect of the digital asset ecosystem. From initial design and security considerations to ongoing maintenance and updates, the wallet software lifecycle plays a pivotal role in providing users with a secure and reliable platform for managing their digital assets.
How do regulatory frameworks impact the cryptocurrency ecosystem?
As the cryptocurrency industry continues to mature, compliance with regulatory frameworks, such as Know Your Customer (KYC) and Anti-Money Laundering (AML) guidelines, has become increasingly important. Crypto wallet providers must navigate these regulatory landscapes to ensure the integrity and legitimacy of their platforms.
What are the emerging trends in crypto wallet technology?
The crypto wallet landscape is constantly evolving, with new technologies and features emerging to enhance user experience, security, and overall functionality. From advancements in multi-signature wallets to the integration of decentralized finance (DeFi) protocols, these emerging trends are shaping the future of digital asset management.
What are the challenges associated with cross-chain interoperability in the cryptocurrency ecosystem?
As the cryptocurrency ecosystem continues to diversify, the ability to seamlessly transfer digital assets across different blockchain networks has become a crucial challenge. Addressing cross-chain interoperability issues is essential for unlocking the full potential of the decentralized finance (DeFi) landscape.
How are blockchain networks addressing the issue of scalability?
As the adoption of cryptocurrencies and blockchain technology grows, the need for scalable solutions to handle the increasing volume of transactions has become paramount. Innovations in layer-2 protocols, sharding, and other scaling techniques are being explored to ensure the long-term viability and efficiency of blockchain networks.


No comments yet